https://tryhackme.com/room/nmap01
Task 1 Introduction
Keine Fragen in diesem Task.
Task 2 Subnetworks
Frage 1:
How many devices can see the ARP Request?
Haben wir alles korrekt eingegeben und die Pakete gesendet, können wir in der Animation sehen, dass vier Geräte den Request erhalten.
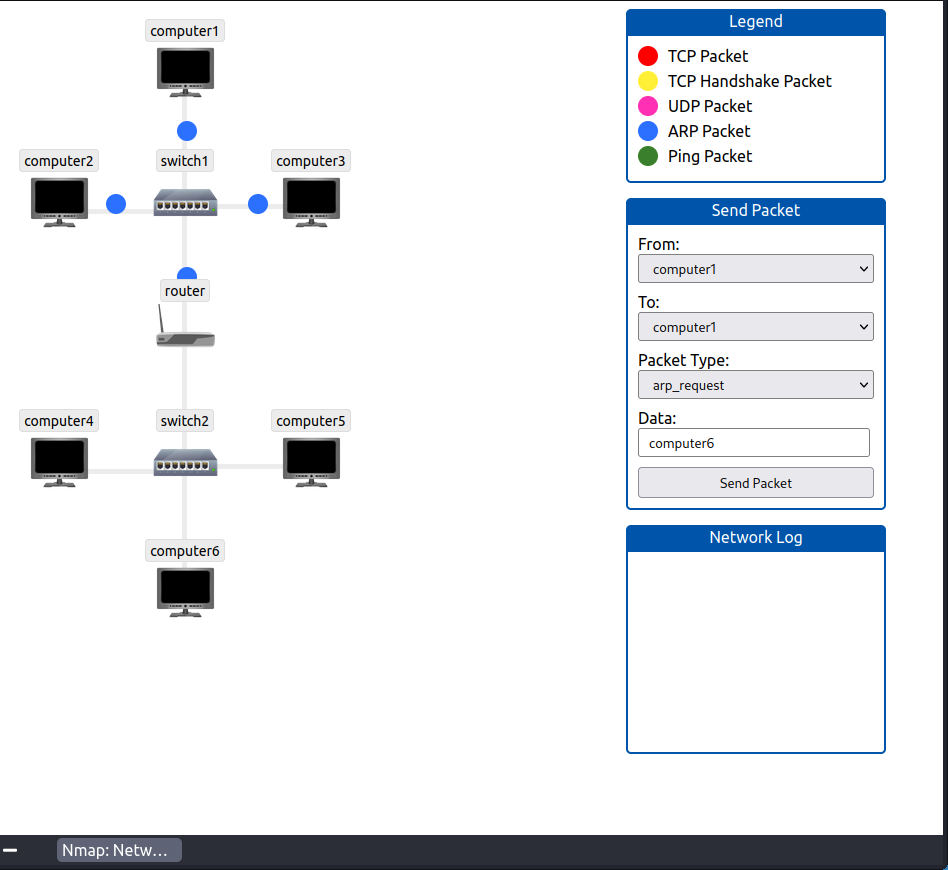
Antwort 1:
4
Frage 2:
Did computer6 receive the ARP Request? (Y/N)
Computer6 hat keinen Request bekommen.
Antwort 2:
n
Frage 3:
How many devices can see the ARP Request?
Auch hier sehen wir die Antwort in den Animation.
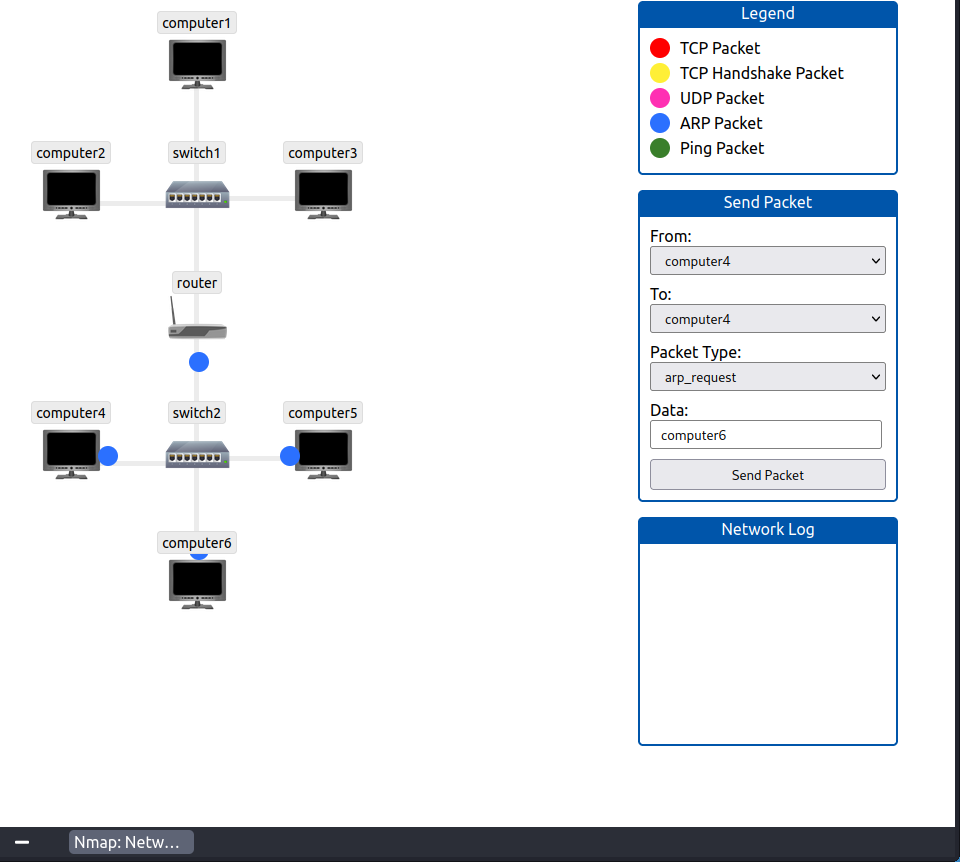
Antwort 3:
4
Frage 4:
Did computer6 reply to the ARP Request? (Y/N)
In der Animation sehen wir Computer6 auch antworten.
Antwort 4:
y
Task 3 Enumerating Targets
Frage 1:
What is the first IP address Nmap would scan if you provided 10.10.12.13/29 as your target?
Wir scannen hierfür die angegebene IP:
└─$ nmap -sL -n 10.10.12.13/29
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-06 18:06 CEST
Nmap scan report for 10.10.12.8
Nmap scan report for 10.10.12.9
Nmap scan report for 10.10.12.10
Nmap scan report for 10.10.12.11
Nmap scan report for 10.10.12.12
Nmap scan report for 10.10.12.13
Nmap scan report for 10.10.12.14
Nmap scan report for 10.10.12.15
Nmap done: 8 IP addresses (0 hosts up) scanned in 0.00 secondsAntwort 1:
10.10.12.8
Frage 2:
How many IP addresses will Nmap scan if you provide the following range 10.10.0-255.101-125?
Auch hier scannen wir wieder die angegebene IP:
└─$ nmap -sL -n 10.10.0-255.101-125
--snip--
Nmap scan report for 10.10.255.124
Nmap scan report for 10.10.255.125
Nmap done: 6400 IP addresses (0 hosts up) scanned in 0.12 secondsAntwort 2:
6400
Task 4 Discovering Live Hosts
Frage 1:
What is the type of packet that computer1 sent before the ping?
Das finden wir im Log:
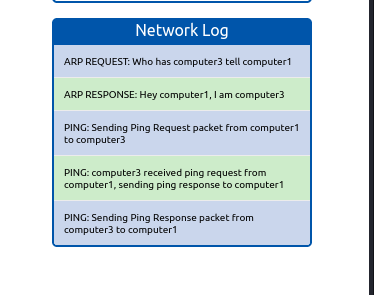
Antwort 1:
ARP Request
Frage 2:
What is the type of packet that computer1 received before being able to send the ping?
Auch das finden wir im Log, an zweiter Stelle.
Antwort 2:
ARP Response
Frage 3:
How many computers responded to the ping request?
Auch das ist im Log zu sehen, nur Computer3 antwortet.
Antwort 3:
1
Frage 4:
What is the name of the first device that responded to the first ARP Request?
Wie wir in der Animation sehen können, antwortet der Router zuerst.
Antwort 4:
router
Frage 5:
What is the name of the first device that responded to the second ARP Request?
Als nächstes antwortet unser angesprochener Computer, Computer 5.
Antwort 5:
Computer5
Frage 6:
Send another Ping Request. Did it require new ARP Requests? (Y/N)
Schicken wir den selben Request ein zweites Mal heraus, sehen wir die direkte Verbindung zu Computer5.
Antwort 6:
n
Task 5 Nmap Host Discovery Using ARP
Frage 1:
How many devices are you able to discover using ARP requests?
Wir bekommen nur Antworten von Computer2, Computer3 und Router.
Antwort 1:
3
Task 6 Nmap Host Discovery Using ICMP
Frage1:
What is the option required to tell Nmap to use ICMP Timestamp to discover live hosts?
Antwort 1:
-PP
Frage 2:
What is the option required to tell Nmap to use ICMP Address Mask to discover live hosts?
Antwort 2:
-PM
Frage 3:
What is the option required to tell Nmap to use ICMP Echo to discover life hosts?
Antwort 3:
-PE
Task 7 Nmap Host Discovery Using TCP and UDP
Frage 1:
Which TCP ping scan does not require a privileged account?
Antwort 1:
TCP SYN Ping
Frage 2:
Which TCP ping scan requires a privileged account?
Antwort 2:
TCP ACK Ping
Frage 3:
What option do you need to add to Nmap to run a TCP SYN ping scan on the telnet port?
Telnet benutzt Port 23.
Antwort 3:
-PS23
Task 8 Using Reverse-DNS Lookup
Frage 1:
We want Nmap to issue a reverse DNS lookup for all the possibles hosts on a subnet, hoping to get some insights from the names. What option should we add?
Antwort 1:
-R
Task 9 Summary
Keine Fragen in diesem Task.