https://app.hackthebox.com/starting-point
Fawn
Task 1:
What does the 3-letter acronym FTP stand for?
Antwort 1:
File Transfer Protocol
Task 2:
Which port does the FTP service listen on usually?
Antwort 2:
21
Mein Weg zur IT Sicherheit
https://app.hackthebox.com/starting-point
Fawn
Task 1:
What does the 3-letter acronym FTP stand for?
Antwort 1:
File Transfer Protocol
Task 2:
Which port does the FTP service listen on usually?
Antwort 2:
21
https://tryhackme.com/room/nmap04
Task 1 Introduction
Keine Fragen in diesem Task.
Task 2 Service Detection
Frage 1:
Start the target machine for this task and launch the AttackBox. Run nmap -sV --version-light 10.10.201.22 via the AttackBox. What is the detected version for port 143?
└─$ sudo nmap -sV --version-light 10.10.201.22
[sudo] password for belcher:
Sorry, try again.
[sudo] password for belcher:
Starting Nmap 7.93 ( https://nmap.org ) at 2022-10-12 18:09 CEST
Nmap scan report for 10.10.201.22
Host is up (0.070s latency).
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u8 (protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http nginx 1.6.2
110/tcp open pop3 Dovecot pop3d
111/tcp open rpcbind
143/tcp open imap Dovecot imapd
Service Info: Host: debra2.thm.local; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.81 secondshttps://tryhackme.com/room/nmap03
Task 1 Introduction
Keine Fragen in diesem Task.
Task 2 TCP Null Scan, FIN Scan, and Xmas Scan
Frage 1:
In a null scan, how many flags are set to 1?
In einem null scan werden keine Flags aktiviert.
Antwort 1:
0
https://tryhackme.com/room/nmap02
Task 1 Introduction
Keine Fragen in diesem Task.
Task 2 TCP and UDP Ports
Frage 1:
Which service uses UDP port 53 by default?
Diese Frage wird nicht im Text erklärt. Für die Antwort müssen wir nachforschen.
Antwort 1:
DNS
https://tryhackme.com/room/nmap01
Task 1 Introduction
Keine Fragen in diesem Task.
Task 2 Subnetworks
Frage 1:
How many devices can see the ARP Request?
Haben wir alles korrekt eingegeben und die Pakete gesendet, können wir in der Animation sehen, dass vier Geräte den Request erhalten.
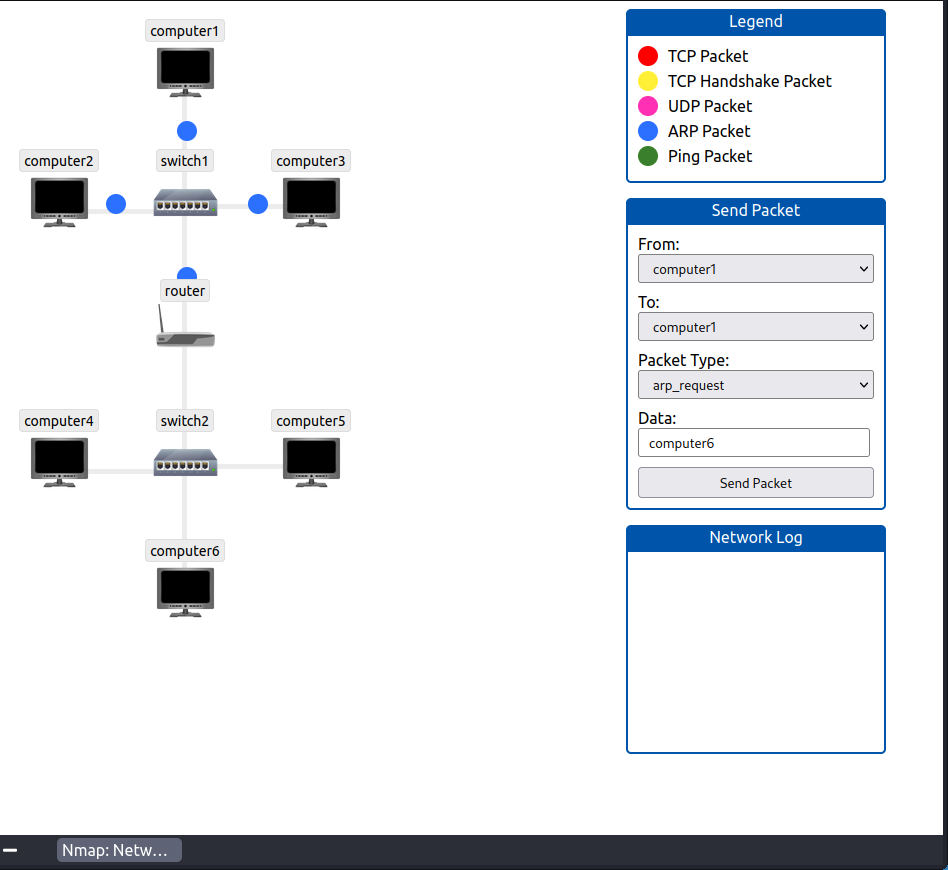
Antwort 1:
4
https://tryhackme.com/room/passiverecon
Task 1 Introduction
Keine Fragen in diesem Task.
Task 2 Passive Versus Active Recon
Frage 1:
You visit the Facebook page of the target company, hoping to get some of their employee names. What kind of reconnaissance activity is this? (A for active, P for passive)
Antwort 1:
p
https://tryhackme.com/room/thelayoftheland
Task 1 Introduction
Kein Fragen in diesem Task.
Task 2 Deploy the VM
Kein Fragen in diesem Task.
Weiterlesenhttps://tryhackme.com/room/enumerationpe
Task 1 Introduction
Frage 1:
What command would you use to start the PowerShell interactive command line?
Antwort 1:
powershell.exe
Task 2 Purpose
Frage 1:
In SSH key-based authentication, which key does the client need?
Antwort 1:
private key
Task 3 Linux Enumeration
Frage 1:
What is the Linux distribution used in the VM?
Nachdem wir uns per SSH mit der Machine verbunden haben setzen wir unser neues Wissen gleich um:
user@red-linux-enumeration:~$ cat /etc/os-release
NAME="Ubuntu"
VERSION="20.04.4 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.4 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focalAntwort 1:
Ubuntu
Frage 2:
What is its version number?
Die Antwort finden wir in der Ausgabe von Frage 1.
Antwort 2:
20.04.4
Frage 3:
What is the name of the user who last logged in to the system?
user@red-linux-enumeration:~$ last
user pts/0 10.8.1.75 Fri Sep 9 15:07 still logged in
reboot system boot 5.4.0-120-generi Fri Sep 9 14:56 still running
reboot system boot 5.4.0-120-generi Mon Jun 20 13:10 - 13:13 (00:02)
randa pts/0 10.20.30.1 Mon Jun 20 11:00 - 11:01 (00:00)
reboot system boot 5.4.0-120-generi Mon Jun 20 09:58 - 11:01 (01:03)
wtmp begins Mon Jun 20 09:58:27 2022Antwort 3:
randa
Frage 4:
What is the highest listening TCP port number?
Hier müssen wir sudo nutzen, da wir sonst nicht alle Ergebnisse angezeigt bekommen:
user@red-linux-enumeration:~$ sudo netstat -antup
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 737/slapd
tcp 0 0 127.0.0.1:6667 0.0.0.0:* LISTEN 718/inspircd
tcp 0 0 10.10.50.96:53 0.0.0.0:* LISTEN 610/named
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 610/named
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN 582/systemd-resolve
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 686/sshd: /usr/sbin
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 610/named
tcp 0 340 10.10.50.96:22 10.8.1.75:42006 ESTABLISHED 1017/sshd: user [pr
tcp6 0 0 :::389 :::* LISTEN 737/slapd
tcp6 0 0 fe80::1e:c8ff:fef5:9:53 :::* LISTEN 610/named
tcp6 0 0 ::1:53 :::* LISTEN 610/named
tcp6 0 0 :::21 :::* LISTEN 633/vsftpd
tcp6 0 0 :::22 :::* LISTEN 686/sshd: /usr/sbin
tcp6 0 0 ::1:953 :::* LISTEN 610/named
udp 0 0 10.10.50.96:68 0.0.0.0:* 579/systemd-network
udp 0 0 0.0.0.0:161 0.0.0.0:* 640/snmpd
udp 0 0 0.0.0.0:53532 0.0.0.0:* 718/inspircd
udp 0 0 10.10.50.96:53 0.0.0.0:* 610/named
udp 0 0 127.0.0.1:53 0.0.0.0:* 610/named
udp 0 0 127.0.0.53:53 0.0.0.0:* 582/systemd-resolve
udp6 0 0 ::1:161 :::* 640/snmpd
udp6 0 0 ::1:53 :::* 610/named
udp6 0 0 fe80::1e:c8ff:fef5:9:53 :::* 610/named Antwort 4:
6667
Frage 5:
What is the program name of the service listening on it?
Die Antwort erhalten wir aus Frage 4.
Antwort 5:
inspircd
Frage 6:
There is a script running in the background. Its name starts with THM. What is the name of the script?
Den Prozess finden wir mit „ps -e“ und etwas suchen, da die Liste etwas länger ist.
Antwort 6:
THM-24765.sh
Task 4 Windows Enumeration
Frage 1:
What is the full OS Name?
Wir loggen uns ein und legen direkt los:
PS C:\Users\user> systeminfo
Host Name: RED-WIN-ENUM
OS Name: Microsoft Windows Server 2019 Datacenter
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: EC2
Registered Organization: Amazon.com
Product ID: 00430-00000-00000-AA155
Original Install Date: 3/17/2021, 2:59:06 PM
System Boot Time: 9/9/2022, 3:28:26 PM
System Manufacturer: Amazon EC2
System Model: t3a.small
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2200 Mhz
BIOS Version: Amazon EC2 1.0, 10/16/2017
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC) Coordinated Universal Time
Total Physical Memory: 2,016 MB
Available Physical Memory: 1,068 MB
Virtual Memory: Max Size: 2,400 MB
Virtual Memory: Available: 1,470 MB
Virtual Memory: In Use: 930 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 30 Hotfix(s) Installed.
--snip--Antwort 1:
Microsoft Windows Server 2019 Datacenter
Frage 2:
What is the OS Version?
Die Antwort erhalten wir aus Frage 1.
Antwort 2:
10.0.17763
Frage 3:
How many hotfixes are installed on this MS Windows Server?
Die Antwort erhalten wir aus Frage 1.
Antwort 3:
30
Frage 4:
What is the lowest TCP port number listening on the system?
PS C:\Users\user> netstat -abno
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:22 0.0.0.0:0 LISTENING 1652
[sshd.exe]
--snip--Antwort 4:
22
Frage 5:
What is the name of the program listening on that port?
Die Antwort erhalten wir aus Frage 4.
Antwort 5:
sshd.exe
Task 5 DNS, SMB, and SNMP
Frage 1:
Knowing that the domain name on the MS Windows Server of IP MACHINE_IP is redteam.thm, use dig to carry out a domain transfer. What is the flag that you get in the records?
└─$ dig -t AXFR redteam.thm @MACHINE_IP
; <<>> DiG 9.18.6-2-Debian <<>> -t AXFR redteam.thm @10.10.28.86
;; global options: +cmd
redteam.thm. 3600 IN SOA red-win-enum. hostmaster. 5 900 600 86400 3600
redteam.thm. 3600 IN NS red-win-enum.
first.redteam.thm. 3600 IN A 10.10.254.1
flag.redteam.thm. 3600 IN TXT "THM{DNS_ZONE}"
second.redteam.thm. 3600 IN A 10.10.254.2
tryhackme.redteam.thm. 3600 IN CNAME tryhackme.com.
redteam.thm. 3600 IN SOA red-win-enum. hostmaster. 5 900 600 86400 3600
;; Query time: 48 msec
;; SERVER: 10.10.28.86#53(10.10.28.86) (TCP)
;; WHEN: Fri Sep 09 17:46:42 CEST 2022
;; XFR size: 7 records (messages 1, bytes 295)Antwort 1:
THM{DNS_ZONE}
Frage 2:
What is the name of the share available over SMB protocol and starts with THM?
Wir verbinden uns wieder per SSH mit der Machine.
PS C:\Users\user> net share
Share name Resource Remark
-------------------------------------------------------------------------------
C$ C:\ Default share
IPC$ Remote IPC
ADMIN$ C:\Windows Remote Admin
Internal C:\Internal Files Internal Documents
THM{829738} C:\Users\user\Private Enjoy SMB shares
Users C:\Users
The command completed successfully.Antwort 2:
THM{829738}
Frage 3:
Knowing that the community string used by the SNMP service is public, use snmpcheck to collect information about the MS Windows Server of IP 10.10.28.86. What is the location specified?
Wir sind wieder auf unserem Kali Rechner und starten snmpcheck. Sollte es bei euch nicht funktionieren (wie zuerst bei mir), stellt sicher, dass ihr perl-tk installiert habt: sudo apt install perl-tk
snmpcheck MACHINE_IP -c public Jetzt öffnet sich ein kleines GUI und snmpcheck legt los. Also in der Theorie. Die GUI Version funktioniert bei mir absolut nicht. Zum Glück gibt es auch eine Command-Line Version:
snmp-check MACHINE_IP -c publicWarnung, es dauer SEHR lange!
└─$ snmp-check 10.10.28.86 -c public
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.10.28.86:161 using SNMPv1 and community 'public'
[*] System information:
Host IP address : 10.10.28.86
Hostname : RED-WIN-ENUM
Description : Hardware: AMD64 Family 23 Model 1 Stepping 2 AT/AT COMPATIBLE - Software: Windows Version 6.3 (Build 17763 Multiprocessor Free)
Contact : TryHackMe
Location : THM{SNMP_SERVICE}
Uptime snmp : 00:21:50.68
Uptime system : 00:21:30.21
System date : 2022-9-9 16:03:56.1
Domain : WORKGROUP
--snip--Antwort 3:
THM{SNMP_SERVICE}
Task 6 More Tools for Windows
Frage 1:
What utility from Sysinternals Suite shows the logged-in users?
Antwort 1:
PsLoggedOn
Task 7 Conclusion
Keine Fragen in diesem Task.
Mit Lichtgeschwindigkeit geht es an den Authentifizierungen vorbei *badum tss*
Task 1 Brief
Der Name sagt alles. Keine Fragen, keine Antworten.
Task 2 Username Enumeration
Frage 1:
What is the username starting with si*** ?
Wir benutzen wieder den vorgegebenen Befehl, passen ihn aber an unsere Verzeichnisse an:
ffuf -w /usr/share/seclists/Usernames/Names/names.txt -X POST -d "username=FUZZ&email=x&password=x&cpassword=x" -H "Content-Type: application/x-www-form-urlencoded" -u http://10.10.138.227/customers/signup -mr "username already exists"Keine Müdigkeit und gleich weiter mit Subdomain Enumeration!
Task 1 Brief
Frage 1:
What is a subdomain enumeration method beginning with B?
Antwort 1:
Brute Force
© 2026 René und IT-Sec
Theme von Anders Norén — Hoch ↑