https://tryhackme.com/room/activerecon
Task 1 Introduction
Keine Fragen in diesem Task.
Task 2 Web Browser
Frage 1:
Browse to the following website and ensure that you have opened your Developer Tools on AttackBox Firefox, or the browser on your computer. Using the Developer Tools, figure out the total number of questions.
Wir besuchen die angegebene Seite und öffnen die Developer Tools (STRG+SHIFT+I). Unter dem Inspector-Reiter sehen wir, dass die Datei „script.js“ für den Chat verantwortlich ist. Nun navigieren wir zu dem Debugger-Reiter und klicken auf die „script.js“, anschließend scrollen wir herunter, um die Anzahl der Fragen zu finden:
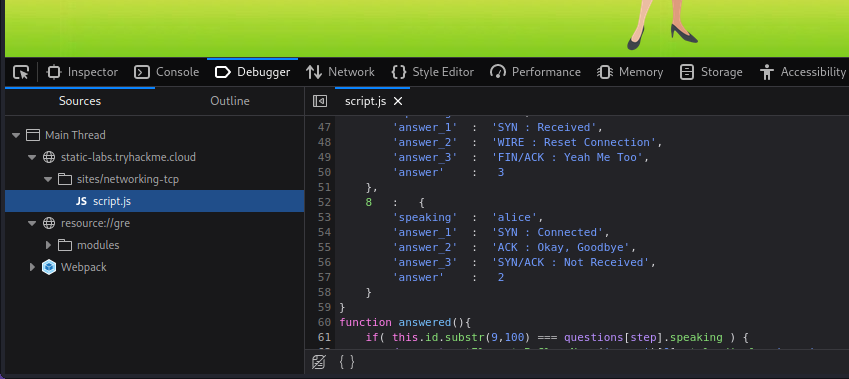
Alternativ können wir uns auch durch die Fragen klicken, diese zählen und eine Flag (THM{TCP_CHATTER}) finden. Diese wird wohl für einen anderen Raum gebraucht.
Antwort 1:
8
Task 3 Ping
Frage 1:
Which option would you use to set the size of the data carried by the ICMP echo request?
Für verschiedene Optionen können wir die manpage aufrufen (man ping):
-s packetsize
Specifies the number of data bytes to be sent. The default is 56, which translates into 64 ICMP data bytes when combined with the 8 bytes of ICMP header data.Antwort 1:
-s
Frage 2:
What is the size of the ICMP header in bytes?
Auch diese Antwort finden wir in der manpage:
ICMP PACKET DETAILS
An IP header without options is 20 bytes. An ICMP ECHO_REQUEST packet contains an additional 8 bytes worth of ICMP header followed by an arbitrary amount of data. When a packetsize is given, this indicates the size of this extra piece of data (the default is 56). Thus the amount of data received inside of an IP packet of type ICMP ECHO_REPLY will always be 8 bytes more than the requested data space (the ICMP header).
If the data space is at least of size of struct timeval ping uses the beginning bytes of this space to include a timestamp which it uses in the computation of round trip times. If the data space is shorter, no round trip times are given.Der ICMP Header macht zusätzliche 8 Bytes aus.
Antwort 2:
8
Frage 3:
Does MS Windows Firewall block ping by default? (Y/N)
Antwort 3:
y
Frage 4:
Deploy the VM for this task and using the AttackBox terminal, issue the command ping -c 10 10.10.70.202. How many ping replies did you get back?
Wir pingen unsere Machine mit dem angegebenen Befehl:
└─$ ping -c 10 10.10.70.202
PING 10.10.70.202 (10.10.70.202) 56(84) bytes of data.
64 bytes from 10.10.70.202: icmp_seq=1 ttl=63 time=88.5 ms
64 bytes from 10.10.70.202: icmp_seq=2 ttl=63 time=85.9 ms
64 bytes from 10.10.70.202: icmp_seq=3 ttl=63 time=76.4 ms
64 bytes from 10.10.70.202: icmp_seq=4 ttl=63 time=74.7 ms
64 bytes from 10.10.70.202: icmp_seq=5 ttl=63 time=73.1 ms
64 bytes from 10.10.70.202: icmp_seq=6 ttl=63 time=91.2 ms
64 bytes from 10.10.70.202: icmp_seq=7 ttl=63 time=69.4 ms
64 bytes from 10.10.70.202: icmp_seq=8 ttl=63 time=88.2 ms
64 bytes from 10.10.70.202: icmp_seq=9 ttl=63 time=77.5 ms
64 bytes from 10.10.70.202: icmp_seq=10 ttl=63 time=75.7 ms
--- 10.10.70.202 ping statistics ---
10 packets transmitted, 10 received, 0% packet loss, time 9014ms
rtt min/avg/max/mdev = 69.409/80.058/91.215/7.230 ms
Antwort 4:
10
Task 4 Traceroute
Frage 1:
In Traceroute A, what is the IP address of the last router/hop before reaching tryhackme.com?
Im ersten Beispiel finden wir die IP in Zeile 14.
Antwort 1:
172.67.69.208
Frage 2:
In Traceroute B, what is the IP address of the last router/hop before reaching tryhackme.com?
Im zweiten Beispiel finden wir die IP in Zeile 26.
Antwort 2:
104.26.11.229
Frage 3:
In Traceroute B, how many routers are between the two systems?
Im zweiten Beispiel benötigen wir 26 hops.
Antwort 3:
26
Frage 4:
Start the attached VM from Task 3 if it is not already started. On the AttackBox, run traceroute 10.10.70.202. Check how many routers/hops are there between the AttackBox and the target VM.
Auch wenn diese Frage keine Lösung fordert, interessant ist es trotzdem:
traceroute 10.10.70.202
traceroute to 10.10.70.202 (10.10.70.202), 30 hops max, 60 byte packets
1 10.8.0.1 (10.8.0.1) 87.683 ms 87.692 ms 87.696 ms
2 10.10.70.202 (10.10.70.202) 90.891 ms 90.914 ms 90.919 msTask 5 Telnet
Frage 1:
Start the attached VM from Task 3 if it is not already started. On the AttackBox, open the terminal and use the telnet client to connect to the VM on port 80. What is the name of the running server?
Wir verbinden uns via Telnet mit unserer Machine und geben dann „GET / HTTP/1.1“ ein und bestätigen 2x mit ENTER:
└─$ telnet 10.10.70.202 80
Trying 10.10.70.202...
Connected to 10.10.70.202.
Escape character is '^]'.
GET / HTTP/1.1
HTTP/1.1 400 Bad Request
Date: Wed, 05 Oct 2022 18:01:42 GMT
Server: Apache/2.4.10 (Debian)
Content-Length: 308
Connection: close
Content-Type: text/html; charset=iso-8859-1
Antwort 1:
Apache
Frage 2:
What is the version of the running server (on port 80 of the VM)?
Diese Antwort erhalten wir aus dem Request in Frage 1.
Antwort 2:
2.4.10
Task 6 Netcat
Frage 1:
Start the VM and open the AttackBox. Once the AttackBox loads, use Netcat to connect to the VM port 21. What is the version of the running server?
Wir verbinden uns via netcat mit unserer Machine auf Port 21:
└─$ nc 10.10.77.53 21
220 debra2.thm.local FTP server (Version 6.4/OpenBSD/Linux-ftpd-0.17) ready.
Antwort 1:
0.17
Task 7 Putting It All Together
Keine Fragen in diesem Task.