https://tryhackme.com/room/windowsapi
Task 1 Introduction
Keine Fragen in diesem Task.
Task 2 Subsystem and Hardware Interaction
Frage 1:
Does a process in the user mode have direct hardware access? (Y/N)
Antwort 1:
n
Frage 2:
Does launching an application as an administrator open the process in kernel mode? (Y/N)
Antwort 2:
n
Task 3 Components of the Windows API
Frage 1:
What header file imports and defines the User32 DLL and structure?
Hier werden wir auf die Wiki-Seite von Windows.h verwiesen, mit dem Hinweis, dass wir mehr Nachforschunen anstellen müssen.
winuser.h – user32.dll: user servicesAntwort 1:
winuser.h
Frage 2:
What parent header file contains all other required child and core header files?
In diesem Fall ist die übergeordnete Header Datei (Parent Header) windows.h. Diese beinhaltet alle anderen Child – und Core – Header Dateien aus dem Wiki-Eintrag.
Antwort 2:
windows.h
Task 4 OS Libraries
Frage 1:
What overarching namespace provides P/Invoke to .NET?
Mit „using System;“, bzw. „System“ laden wir P/Invoke.
Antwort 1:
System
Frage 2:
What memory protection solution obscures the process of importing API calls?
ASLR (Address Space Layout Randomization) verschleiert den Prozess.
Antwort 2:
ASLR
Task 5 API Call Structure
Frage 1:
Which character appended to an API call represents an ANSI encoding?
Antwort 1:
A
Frage 2:
Which character appended to an API call represents extended functionality?
Antwort 2:
Ex
Frage 3:
What is the memory allocation type of 0x00080000 in the VirtualAlloc API call?
Wir öffnen die Seite der API Dokumentation und geben im Suchfeld „0x00080000“ ein. Unter den Ergebnissen suchen wir nun das mit „VirtualAlloc function“ und öffnen die Seite. Auf dieser Scrollen wir herunter, bis wir unseren gesuchten Wert gefunden haben.
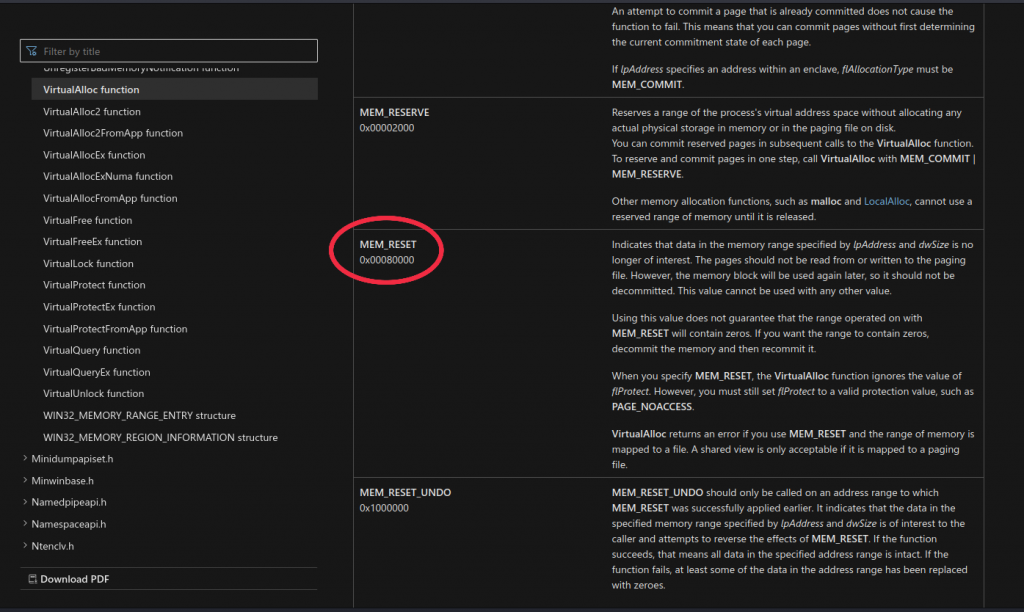
Antwort 3:
MEM_RESET
Task 6 C API Implementations
Frage 1:
Do you need to define a structure to use API calls in C? (Y/N)
Antwort 1:
n
Task 7 .NET and PowerShell API Implementations
Frage 1:
What method is used to import a required DLL?
Antwort 1:
DLLImport
Frage 2:
What type of method is used to reference the API call to obtain a struct?
Hier müssen wir wieder einen Blick in Task 4 werfen.
Antwort 2:
External
Task 8 Commonly Abused API Calls
Frage 1:
Which API call returns the address of an exported DLL function?
Antwort 1:
GetProcAddress
Frage 2:
Which API call imports a specified DLL into the address space of the calling process?
Antwort 2:
LoadLibraryA
Task 9 Malware Case Study
Frage 1:
What Win32 API call is used to obtain a pseudo handle of our current process in the keylogger sample?
Antwort 1:
GetCurrentProcess
Frage 2:
What Win32 API call is used to set a hook on our current process in the keylogger sample?
Antwort 2:
SetWindowsHookEx
Frage 3:
What Win32 API call is used to obtain a handle from the pseudo handle in the keylogger sample?
Antwort 3:
GetModuleHandle
Frage 4:
What Win32 API call is used unset the hook on our current process in the keylogger sample?
Antwort 4:
UnhookWindowsHookEx
Frage 5:
What Win32 API call is used to allocate memory for the size of the shellcode in the shellcode launcher sample?
Antwort 5:
VirtualAlloc
Frage 6:
What native method is used to write shellcode to an allocated section of memory in the shellcode launcher sample?
Antwort 6:
Marshal.Copy
Frage 7:
What Win32 API call is used to create a new execution thread in the shellcode launcher sample?
Antwort 7:
CreateThread
Frage 8:
What Win32 API call is used to wait for the thread to exit in the shellcode launcher sample?
Antwort 8:
WaitForSingleObject
Task 10 Conclusion
Keine Fragen in diesem Task.